Put patient feedback at the heart of your care delivery
Imagine if healthcare teams could hear and make use of the observations and perspectives of their patients, no matter who they are and where they are.
With Cemplicity, they can.
Put patient feedback at the heart of your care delivery
Imagine if healthcare teams could hear and make use of the observations and perspectives of their patients, no matter who they are and where they are.
With Cemplicity, they can.
“This is giving clinicians a chance to embrace the positive feedback, and identify areas where they could improve.”
“Overall, the Cemplicity programme provides us with valuable insights into the effectiveness of our client services from a client experience perspective.”
“The team is great to work with and always up for the challenge of innovating. Your strong values of patient-first and values-based healthcare, really align with our System priorities. It is clear your team is driven to ensure our collective efforts significantly impact our population and clinical teams.”
“Using the Cemplicity platform we’re able to respond immediately. It allows us to collect quantitative data, but also gather patient stories which allow us to improve our service in a very timely way.”
“Cemplicity as a company are brilliant to work with. They are passionate about using Outcomes to improve patient care. The platform is very easy for clinicians to use.”
Act on patient insight beyond the clinical setting
Make full use of your patients’ valuable observations and perspectives, no matter who they are and where they are.
Our proven system keeps patients constantly engaged, so you’ll hear every single patient’s voice throughout their care journey.
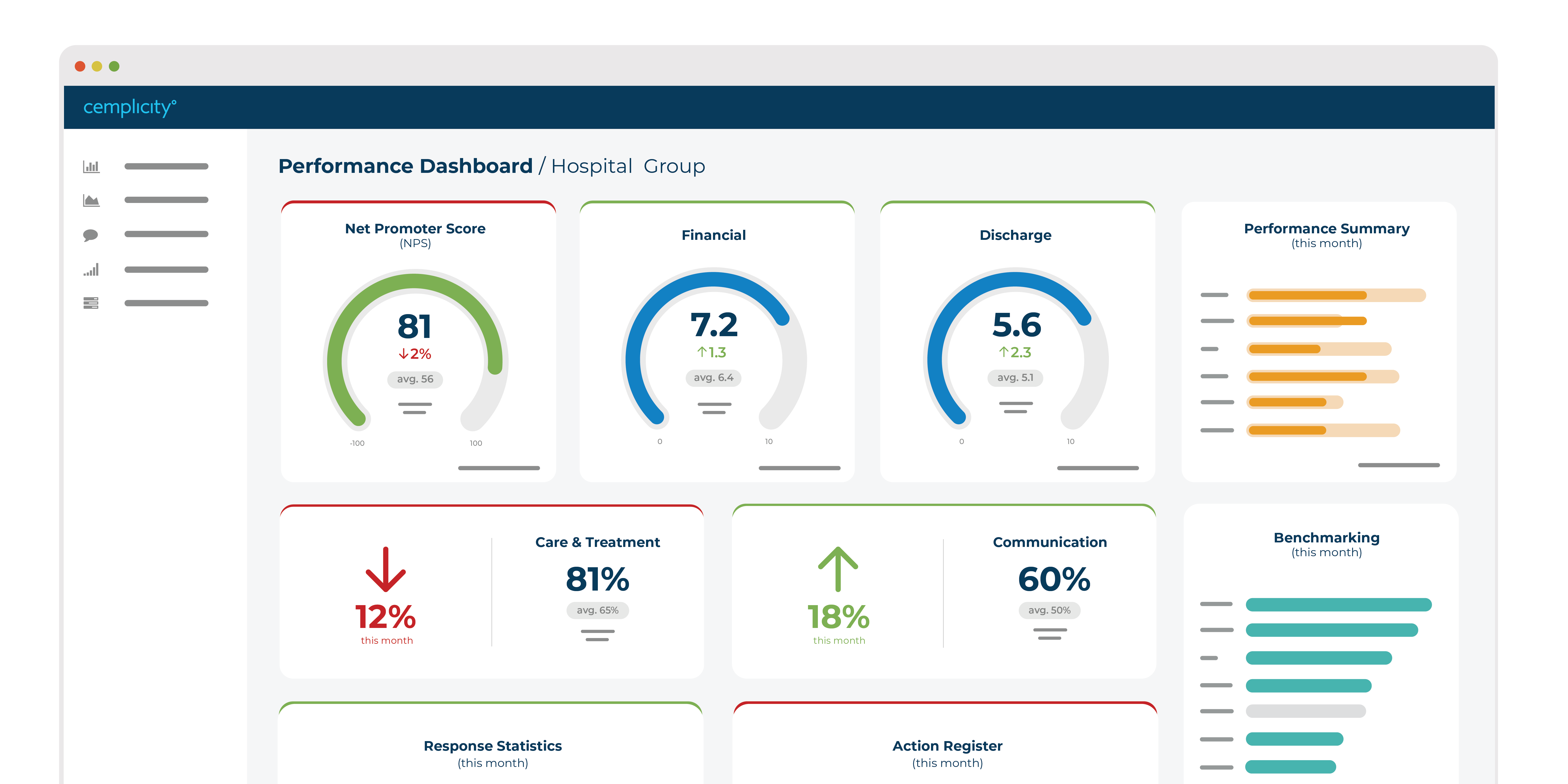
Turn patient observations into actionable data
With intuitive data dashboards, powerful real-time alerting and industry-leading analysts, Cemplicity provides actionable insight for care teams, managers, executives and researchers by capturing what’s important to your patients.

Built with healthcare, for healthcare
Cemplicity was built from the ground up to address the specific needs of healthcare, and is proven in real world settings, not just research projects.
Our team are experts at designing patient-led improvement programmes for all sorts of healthcare organisations.
“This is giving clinicians a chance to embrace the positive feedback, and identify areas where they could improve.”
Southern Cross Healthcare Society